-
Fraud Mitigation & Data Integrity
Essential tools for trust, integrity, fraud prevention & regulatory compliance.
- Driving Confidence in Telecom Through the Trust Framework
- RealNumber DNO – Prevent Fraud on Voice & Text
- RealAgent – Avoid Potential TCPA Violations
- RealBrand – Reinforce a Phone Number’s Identity & Reputation
- Global Number Range – Gain Authoritative Number Intelligence
- Live Status – Query Real-Time Mobile Number Intelligence
- Number Portability Query – Access Accurate Local & Global Number Portability Details
-
Routing Optimization
Gain access to authoritative routing data to create the ultimate routing intelligence for your traffic.
-
Number Administration
Empowering connectivity as the FCC appointed administrators for critical numbering registries.
-
Connected Device Intelligence
Gain total transparency to your IoT assets’ current state and vulnerabilities.
Insights
The Need for Enhanced Caller Authentication: Understanding the Roles of Call Labeling, Signing and Rich Call Data
Phone numbers have evolved into a vital part of our digital identities, serving as a primary means for businesses to connect with their customers. As these interactions have become more central to communications, the challenges of maintaining trust have also grown. Fraud and impersonation via telephone number spoofing continue to disrupt these connections, eroding consumer confidence and making it harder for legitimate businesses to reach their audience. Consumers are bombarded with brand impersonation calls and text messages and, in many cases, being defrauded, turning trust into a scarce commodity. When consumers lose trust in the information displayed on their phones, they simply stop answering calls, causing businesses to miss valuable connections.
But how does a phone know whether to display a 10-digit number, a business name or a label of ‘spam likely’? To understand how this works, let’s take a closer look at three elements: call labeling, call signing and Rich Call Data (RCD).
Call Labeling
Call labeling is the process of assigning labels to incoming pho ne calls or text messages to indicate their potential legitimacy or risk. Common tags include “Spam Likely,” “Potential Spam” or “SCAM,” and were meant to help consumers identify and filter unwanted or suspicious calls. These labels are generated by analytics-based system. While initially introduced to help consumers identify suspicious calls, call labeling often mislabel legitimate calls. Using algorithms based on call patterns, call frequency and historical data, labeling systems frequently assign negative scores to even well-intentioned calls, creating a significant disconnect between the intended purpose of these labels and consumer perception. As a result, businesses struggle to maintain their communications channels, and consumers lose trust in the information displayed on their devices.
ne calls or text messages to indicate their potential legitimacy or risk. Common tags include “Spam Likely,” “Potential Spam” or “SCAM,” and were meant to help consumers identify and filter unwanted or suspicious calls. These labels are generated by analytics-based system. While initially introduced to help consumers identify suspicious calls, call labeling often mislabel legitimate calls. Using algorithms based on call patterns, call frequency and historical data, labeling systems frequently assign negative scores to even well-intentioned calls, creating a significant disconnect between the intended purpose of these labels and consumer perception. As a result, businesses struggle to maintain their communications channels, and consumers lose trust in the information displayed on their devices.
For example, an algorithm might evaluate the following call patterns:
-
All numbers, whether new, ported or reassigned, begin with a negative score. This indicates that, due to a lack of history, the number should be treated with caution and may be labeled as spam.
-
After a number has completed three calls with an end user, it may receive a neutral assessment, meaning the analytics provider will not label the call as spam.
-
Calls with scores higher than zero would have their Caller ID (or CNAM) displayed.
The challenge, however, with call labeling is that numbers with good intent will likely be labeled as spam or scam until they show patterns of good behaviors in the ecosystem. Consumers often assume these labels reflect bad behavior, which creates a disconnect between the intended use of labels and consumer perception of that number. This discrepancy between how the ecosystem is using labels continues to erode trust with consumers.
STIR/SHAKEN: Call Signing
 In response to the growing threat of call spoofing, the telecommunications industry introduced the STIR/SHAKEN framework to authenticate phone calls using digital signatures. STIR (Secure Telephone Identity Revisited) focuses on the technical verification of call authenticity through cryptographic signatures, while SHAKEN (Signature-based Handling of Asserted Information Using Tokens) manages the digital signature process.
In response to the growing threat of call spoofing, the telecommunications industry introduced the STIR/SHAKEN framework to authenticate phone calls using digital signatures. STIR (Secure Telephone Identity Revisited) focuses on the technical verification of call authenticity through cryptographic signatures, while SHAKEN (Signature-based Handling of Asserted Information Using Tokens) manages the digital signature process.
While STIR/SHAKEN was a promising first step toward building trust, it has not fully addressed the root issues of trust in communications. One of the major shortcomings is the absence of a robust Know Your Customer (KYC) process, which would ensure proper vetting of enterprises and establish their legitimate Right-To-Use (RTU) of the number. Without verifying the association between enterprises and their phone numbers, STIR/SHAKEN falls short of ensuring that calls are not only authenticated but also trusted.
Additionally, STIR/SHAKEN operates within a fragmented environment where calls must pass through multiple service providers, each using different analytics and verification processes. The inconsistency across providers complicates the process and leads to a lack of uniform rules for call acceptance and rejection.
Enterprise Call Signing with Right to Use
The STIR/SHAKEN framework includes an additional tool designed specifically for the types of calls that enterprises and businesses typically make and receive. Delegate certificates were added to the STIR/SHAKEN framework to allow for Enterprise businesses to be “delegated” the responsibility to represent their right to use of their assigned telephone number resources. This is deployed via call signing and the STIR/SHAKEN identity header. A delegate certificate can be used to protect the integrity of the telephone number used for a call directly from the point of origination in the enterprise, thereby providing another layer of trust to the called party.
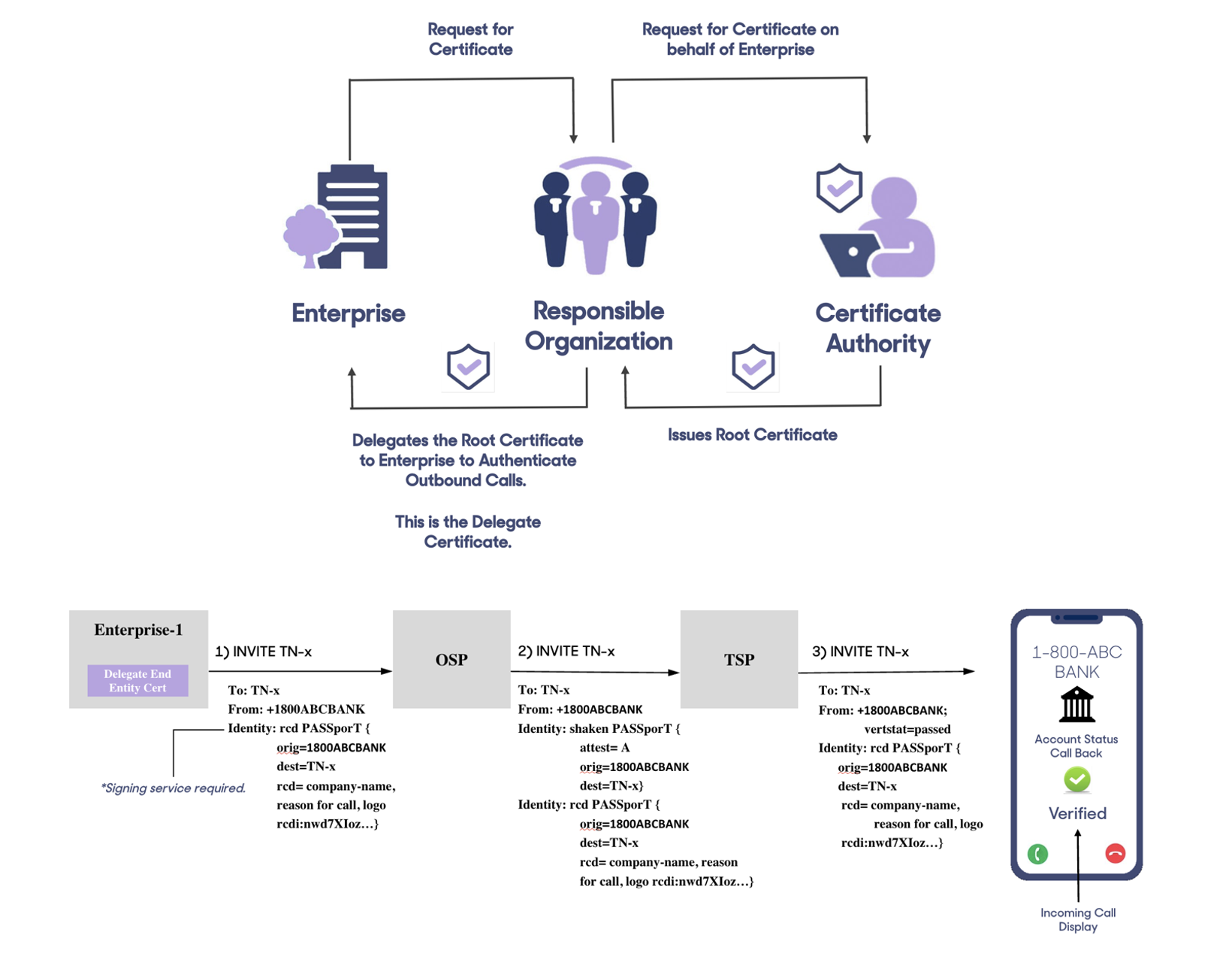
Rich Call Data (RCD)
The industry has also made strides in improving the presentation of caller information through proprietary implementations of Rich Call Data (RCD), sometimes referred to as Branded Calling. RCD enables the display of more comprehensive information, such as a business name, logo and even the reason for the call, which can help users identify legitimate communications.
However, proprietary RCD solutions suffer from a lack of standardization. Different providers handle RCD in varying ways, resulting in inconsistencies across networks and devices. Moreover, without proper vetting and KYC processes, there is a risk that even fraudulent calls could present RCD, further complicating the trust landscape. This fragmented approach undermines the potential benefits of RCD and diminishes consumer trust.
So how do we build Trust in Calling?
While Call Labeling, STIR/SHAKEN Call Signing and RCD have good intentions of supporting call authentication, they come with challenges and limitations. One way to address these limitations is the expansion of the framework that the telecom ecosystem leverages to present calls to end users. Currently, there are Proof of Concepts (POC) initiatives in market that utilize telephone number authorized delegate certificates. These delegate certificates enable the party with the right to use a telephone number to be an authorized signer representing a trusted presentation to any terminating service provider authenticating a call end-to-end. Today, calls that lack a trusted delegate certificate are not being blocked, but the industry is moving toward a broader adoption of this practice to help prevent fraudulent calls from reaching a consumer. This non-monopolistic approach is establishing a more trusted framework, helping to restore confidence in the telecom ecosystem.
The future of enterprise calling lies in collaboration, transparency and standardization. By embracing a Trust Framework that combines STIR/SHAKEN, vetted enterprise identities and trusted Rich Call Data, the telecommunications industry can restore consumer confidence and ensure that businesses can reach their customers without fear of their calls being mislabeled or rejected.
To learn more about the Trust Framework, visit https://www.somos.com/driving-trust-communications.
Stay Connected
Stay in touch! Sign up for our monthly newsletter.
Need to reach us sooner? Call, text, or email us at:
844.HEY.SOMOS help@somos.com